Aug
28
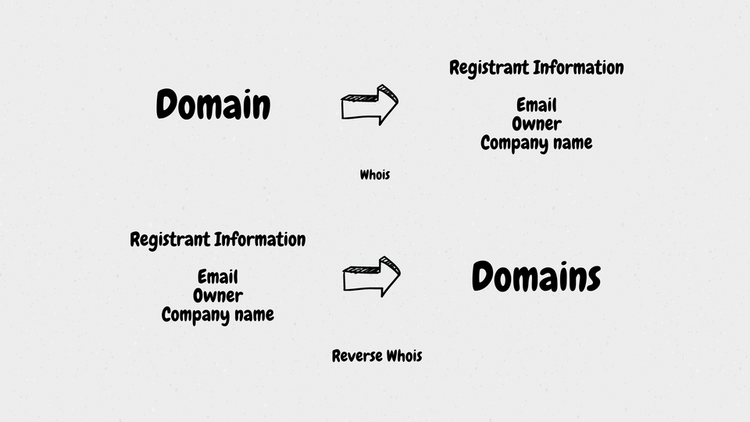
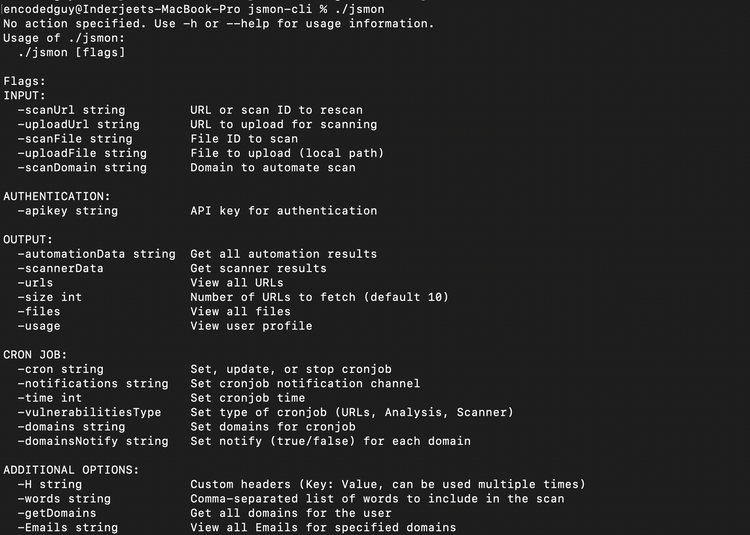
jsmon-cli - Enhanced Security Tooling for JavaScript (jsmon.sh)
4 min read
Feb
13
How I Got Multiple Privilege Escalations - The Easy Trick?
2 min read
Nov
24
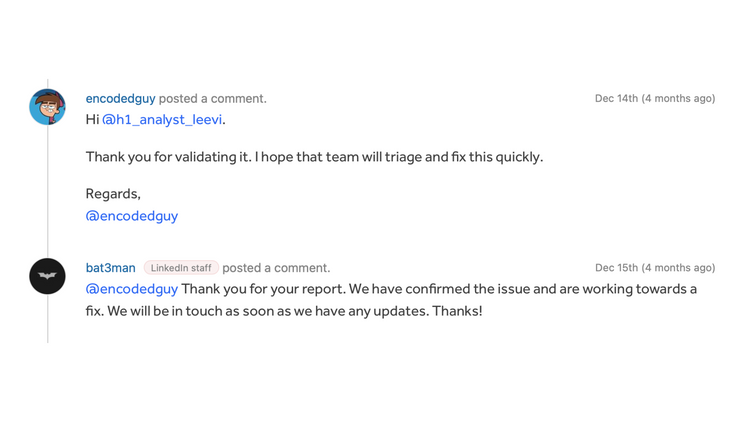
Discovering private chats between users and the support team
5 min read
Oct
13
Android Hacking: The libwebp Vulnerability (zero-day/zero-click)
4 min read
Oct
13
Soft Deletion of Resources - [Privacy Violation]
3 min read
Sep
23
Binary Exploitation: 64-bit Buffer Overflow Attack
8 min read
Aug
25
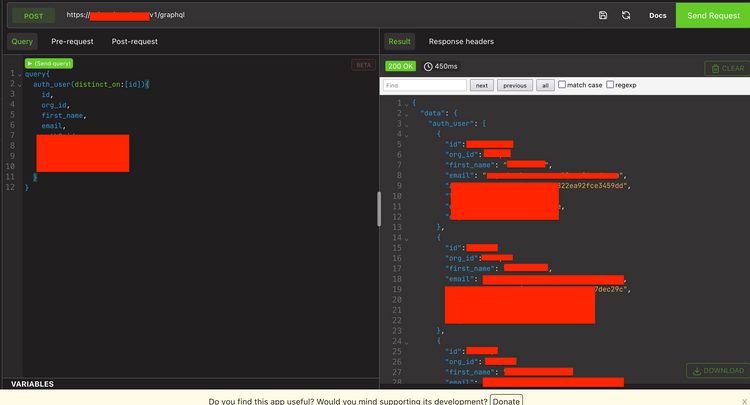
API Excessive Data Exposure: Why Devs? Why?
1 min read
Aug
10
5500$ Bug Story - Ezzy 2FA Bypass
1 min read
Jun
30
Default OTP: Account Takeover
1 min read
Jun
24
Unmasking Scammers
4 min read
Jun
20
Bypassing Okta SSO=> HTTPS/HTTP
1 min read
Jun
14
Pwning Admin Panel To Change Movie Ticket Prices at Disney
1 min read
May
31
The Impact of XSS on SEO and Website Reputation: Strategies for Recovery and Prevention
3 min read
May
28
Slides: GraphQL Hacking
3 min read
May
27
Changing Others Profile Pic with IDOR
2 min read
May
23
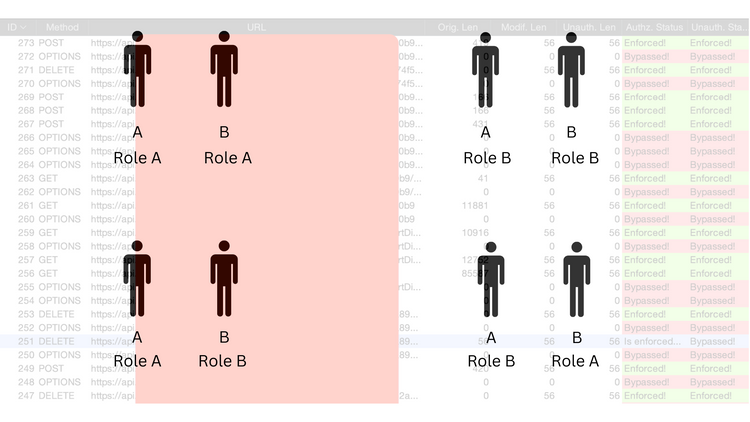
[1->2->3] or [2->3]: Bypassing Authentication Barriers
3 min read
Apr
25
Tools for reconnaissance and footprinting
4 min read
Apr
17
Why Shift to Manual Hacking?
4 min read
Apr
12
Writeup: Delete Replies on LinkedIn Learning
2 min read
Apr
04
Guide to Parameter Enumeration
5 min read

![Soft Deletion of Resources - [Privacy Violation]](/content/images/size/w750/2023/10/username.png)




![[1->2->3] or [2->3]: Bypassing Authentication Barriers](/content/images/size/w750/2023/05/Delete-your-account.png)