Changing Others Profile Pic with IDOR

Hi folks! Hope you are doing great. This is Aravind (aravind0x7) here with an awesome write-up. I will discuss about one of my past finding on target.com(can’t reveal site here) where I was able to change the profile picture of any user of that website by just knowing their user id. Isn’t it cool? Let’s start the journey.
If you are a experienced hacker, then by this time you might have catched the type of vulnerability that existed on target.com. Anyways the main reason for this issue was “Insecure Direct Object Reference” IDOR, Already heard somewhere ? If not get know about it here.
https://portswigger.net/web-security/access-control/idor
Jumping into my finding, target.com had all the basic things like all other websites have. It had a account page which carries all information about the user and you can also set your own profile picture for your account. At first I tried to inject a XSS payload which was in .png format, into the upload field but nothing worked out. While watching the requests and responses with burp. I noticed that when we upload a pic, the user id is mentioned in the request. After seeing this I got an idea to change my user id to somebody else user id. Quickly I created another account and tested the same.
I made another account, captured the user id (say user 2) and stored it elsewhere. Now I went back to my previous account (say hacker) and uploaded the profile pic by changing my user id to the user id I took from user 2.
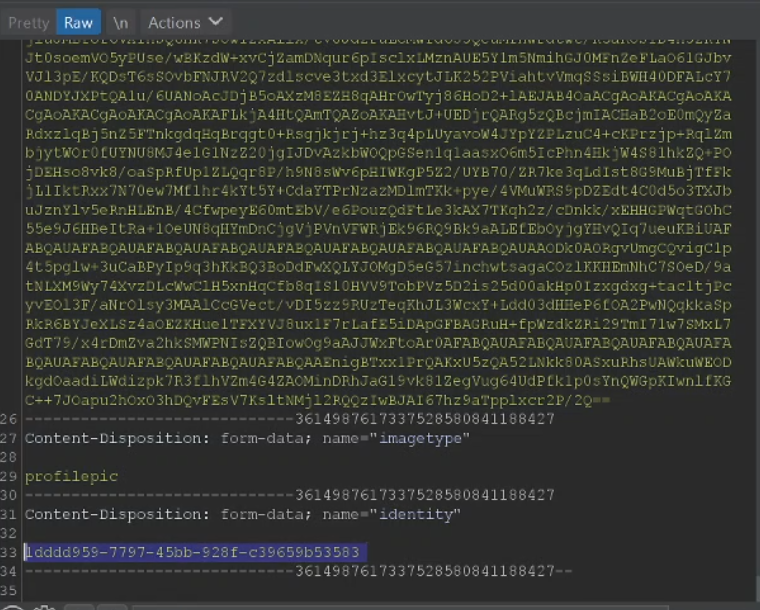
I was surprised to see that, the victims profile picture is changed now by just changing the user id. Quickly I made a report and submitted it to the security team of the website. That's a short story of my finding and I hope that you guys got some idea about hunting IDOR bugs. Let's catch-up soon in another blog. For more write-ups like this, subscribe and stay tuned.
Wanna get connected ? Visit here www.aravind0x7.in