Guide to Parameter Enumeration

Hi folks! I am Inderjeet Singh aka encodedguy. In this blog, I will write about parameter enumeration, its importance, and the automated/manual approach for enumerating parameters.
Introduction
A parameter in a URL is a string of characters that follows a question mark (?) within the URL. Parameters are used to pass information between the client and the server that hosts the website. Parameters are composed of a key-value pair, where the key and value are separated by an equals sign (=).
https://redacted.com/search?param=valueHere, param is the parameter and value is the value for that parameter.
https://www.youtube.com/watch?v=RzVIHpZvVNk
https://crt.sh/?q=yahoo.comTwo examples from youtube and crtsh. Most people are interacting with 1000+ parameters daily while using the Web, but very few notices them in the browser.
Parameter Enumeration
I will try to show why enumerating parameters is important with below 2 examples.
https://target.com/users -> 404 Not Found
https://target.com/users?username=encodedguy -> 200 OKExample: /users gives 404 Not Found. Whereas, /users?useraname=encodedguy gives 200 OK in response. This happens at many web servers, you will hit an endpoint but the response will be 404 and supply a parameter (in-use), and you will get a 200 OK response.
https://target.com/users?sort=ASC -> sorts in ascending order
https://target.com/users?username=encodedguyIn the first case, the attacker only knows the sort parameter is there. Maybe this parameter is using client-side JS to sort the user's list. The username parameter was not known, but using enumeration techniques we got this. And this parameter interacts with the database to get the data of encodedguy the user. Well, now you can try SQL Injection.
Suppose there is a parameter isAdmin that you don't know that it exists, but it does. Set its value to true and you are an admin now. What!!!
I think this gives you an intuition of why parameters are important. Parameter enumeration is a very crucial task and so few hackers focus on this area. You have to enumerate parameters on every endpoint or directory. And that's a pretty hectic task. Right?
Arjun
Arjun is a parameter discovery tool created by @s0md3v. This tool can discover parameters in a directory or endpoint using a wordlist of parameters.
Installation:
pip3 install arjunUsage:
## Using against a single URL with 10 threads:
$ arjun -u https://example.com/api/endpoint -t 10
## Specify HTTP methods with the URL:
$ arjun -u https://example.com/api/endpoint -m <GET/POST/JSON/XML>
## Specifying injection point inside the POST data body:
$ arjun -u https://example.com/endpoint -m JSON --include='{"root":{"a":"b",$arjun$}}'
## Specify custom HTTP headers:
$ arjun -u https://example.com/endpoint --headers "API-KEY: 1231241231212"
## Running against multiple targets and output results
$ arjun -i targets.txt -oJ result.json
$ arjun -i targets.txt -oT results.txt
## Send the results to burp proxy
$ arjun -i targets.txt -oB 127.0.0.1:8080Source Link: https://github.com/s0md3v/Arjun
ParamMiner
ParamMiner can be used to identify hidden parameters, which are not visible on the web page but can be accessed through HTTP requests. ParamMiner works by analyzing a set of HTTP requests and responses captured using a proxy tool, such as Burp Suite or OWASP ZAP.
Source Link: https://github.com/PortSwigger/param-miner
Installation:
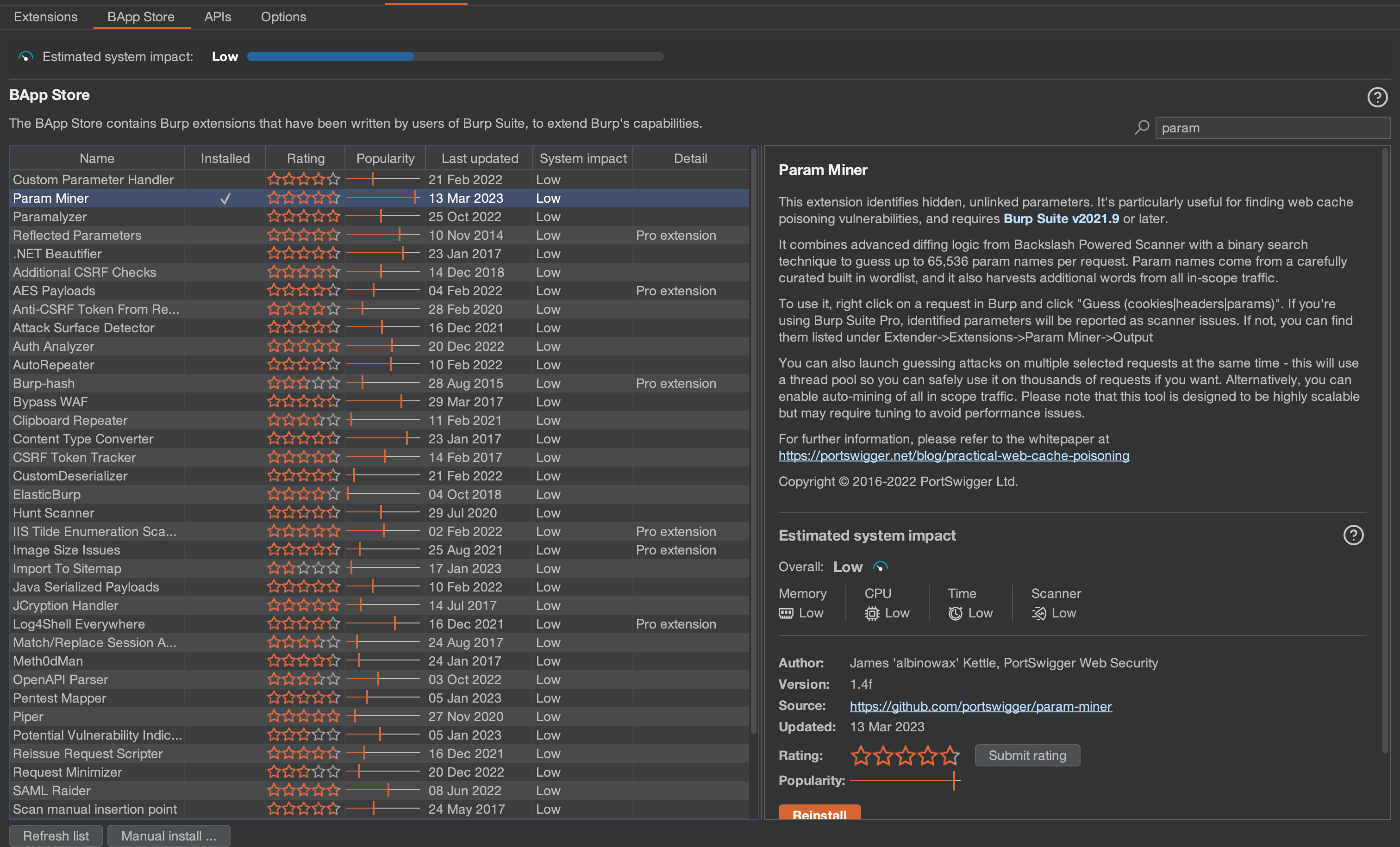
Go to your Burpsuite Extender Tab and in the BApp Store search Param Miner. Click on Install to install this extension.
Usage:
Go to your Proxy Tab -> HTTP History. Select any of the HTTP requests whose parameters you need to discover. Right click -> Extensions -> Param Miner -> Guess params -> Guess GET parameters.
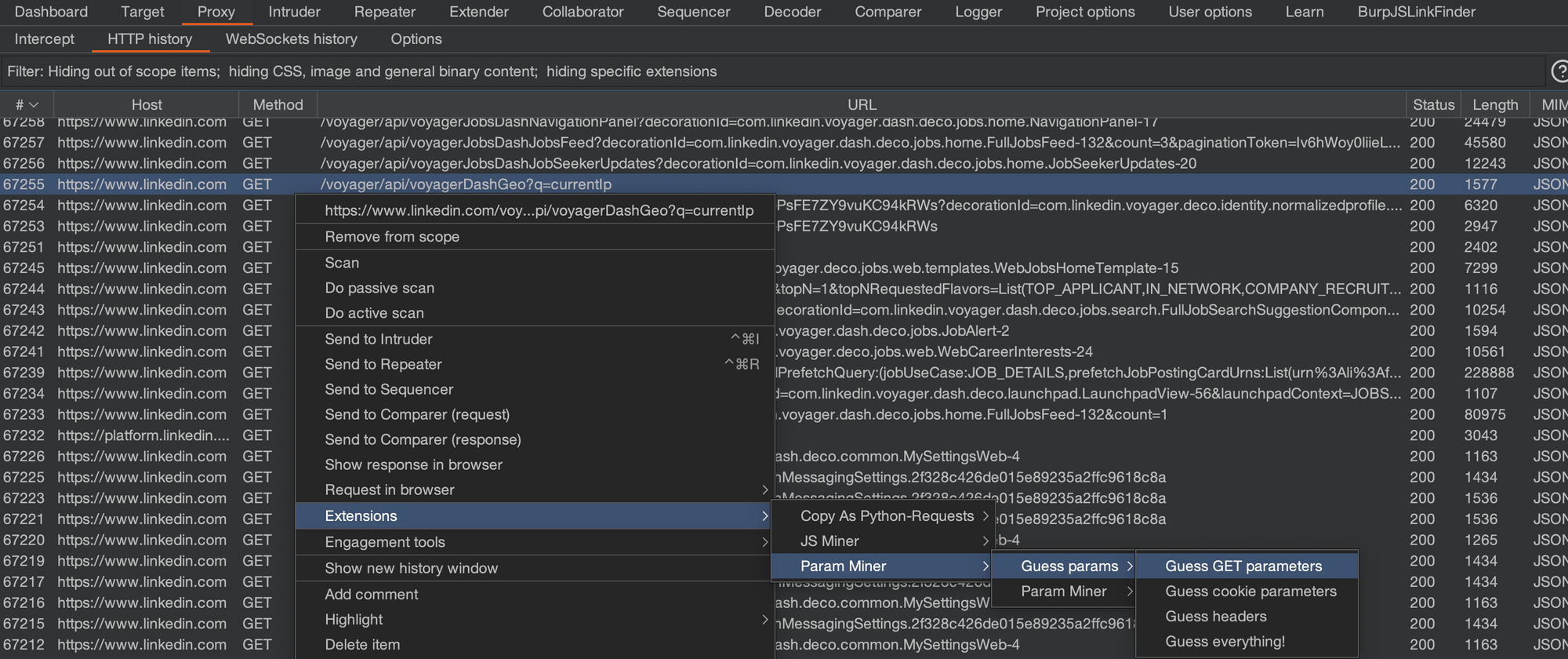
ParamMiner is so useful. Like, it can give you unkeyed inputs (useful for web cache poisoning). It can also guess parameters in cookies and headers. There are way more options in Param Miner that I would not dive into today.
The more you use something, the more better you get at it!!
Manual Enumeration
Create a custom wordlist of parameters. Use ffuf or Burpsuite Intruder to fuzz for parameters.
How do I create a custom wordlist?
If you are already familiar with cut, tr, sed, tee, etc. Linux commands are used for formatting text then this one is easy.
Step 1: Hack the program for days and log more than 10000 HTTP requests at least in your HTTP history. Select all requests and click on Copy URLs. You can also go to Sitemap to Copy URLs.
Step 2: Use your Linux skills now!!
$ cat burp-urls.txt| grep '?' | wc -l
$ cat burp-urls.txt | cut -d'/' -f4-100 | grep '?' | tr '&' '\n' | tr '/' '\n' |tr '?' '\n' | tr '=' '\n' | sort -u | wc -l
$ cat burp-urls.txt | cut -d'/' -f4-100 | grep '?' | tr '&' '\n' | tr '/' '\n' |tr '?' '\n' | tr '=' '\n' | sort -u | tee params.txtHow to fuzz parameters using ffuf?
I have already published another blog on using ffuf with so many practical examples. If you have already read that, then this is very easy for you.
$ ffuf -u https://example.com/endpoint?FUZZ=abc123 -w params.txtUsing -u for specifying URL and FUZZ keyword to specify the place where fuzzing will occur and -w for providing a wordlist to fuzz.

How to fuzz parameters using Burpsuite Intruder?
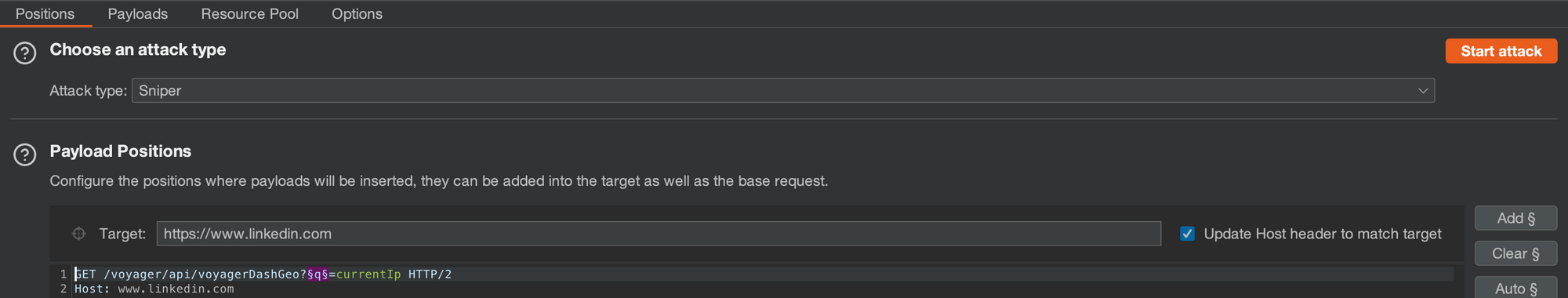
Send the HTTP request to Intruder and specify parameters like keywords to fuzz. Add a wordlist and toggle your rate settings. Attack!!
Conclusion:
Arjun and paramminer work better, but sometimes you need that manual approach because parameter names are unusual, or uncommon. Also, when you are manually fuzzing using Burpsuite Intruder you can visually see the request and it's easy to specify the parameter to FUZZ even if it's inside the POST body.
I personally use a mix of Arjun, ffuf and Intruder most of the time. Param Miner, mostly for web cache vulnerabilities.
Author: Inderjeet Singh
Find me at twitter://3nc0d3dGuY
Happy Hacking!!
