ffuf - Fuzz The Web

Introduction:
ffuf, is a web fuzzer written in Golang by @joohoi. Hackers use ffuf to fuzz directories, subdomains, virtual hosts, usernames, passwords, cookies, anything inside a HTTP request. The tool requires URL or HTTP request, and a wordlist to fuzz.
Working:
FUZZ is the secret. You need to put the word "FUZZ" wherever you want to fuzz, and provide a wordlist. You want to fuzz subdomains, input will be https://FUZZ.target.com with a wordlist of subdomains. You want to fuzz endpoints of a REST API, input will be https://target.com/api/v1/FUZZ with a wordlist of api endpoints.
Installation Ways:
- Go Installation
$ go install github.com/ffuf/ffuf/v2@latest- Download binary from Releases
Go to https://github.com/ffuf/ffuf/releases- MacOS brew Installation:
$ brew install ffuf- Compile and Build
$ git clone https://github.com/ffuf/ffuf
$ cd ffuf
$ go get
$ go buildBasic Usage:
Fuzzing directories
-w option for providing a wordlist and -u option to provide a URL. Here, I am fuzzing directories because the keyword FUZZ is present at directory location.
$ ffuf -w <wordlist.txt> -u https://<target.com>/FUZZ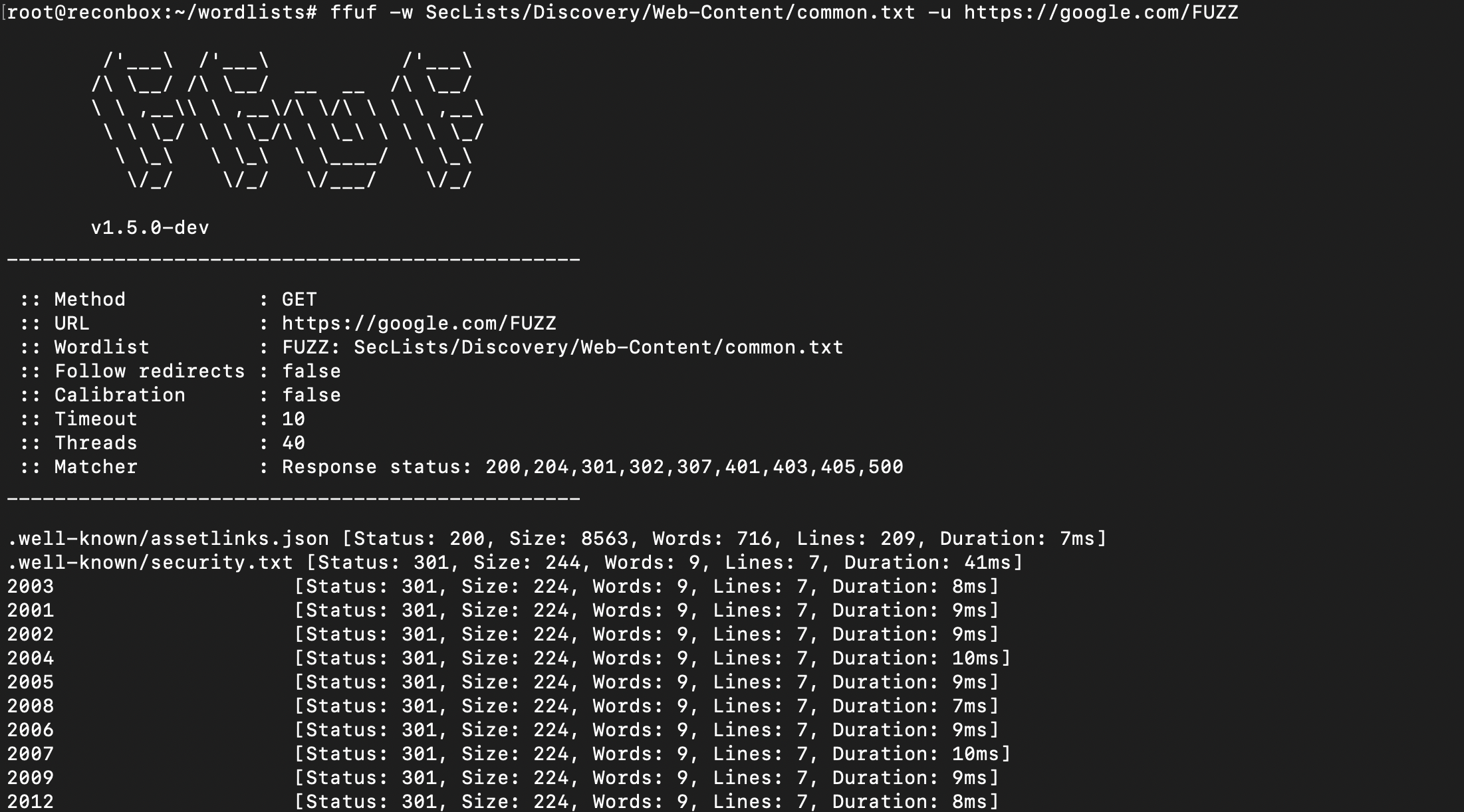
Basic Filters/Matchers
To remove 301 status code results, use -fc option (filter code)
$ ffuf -w <wordlist.txt> -u https://<target.com>/FUZZ -fc 301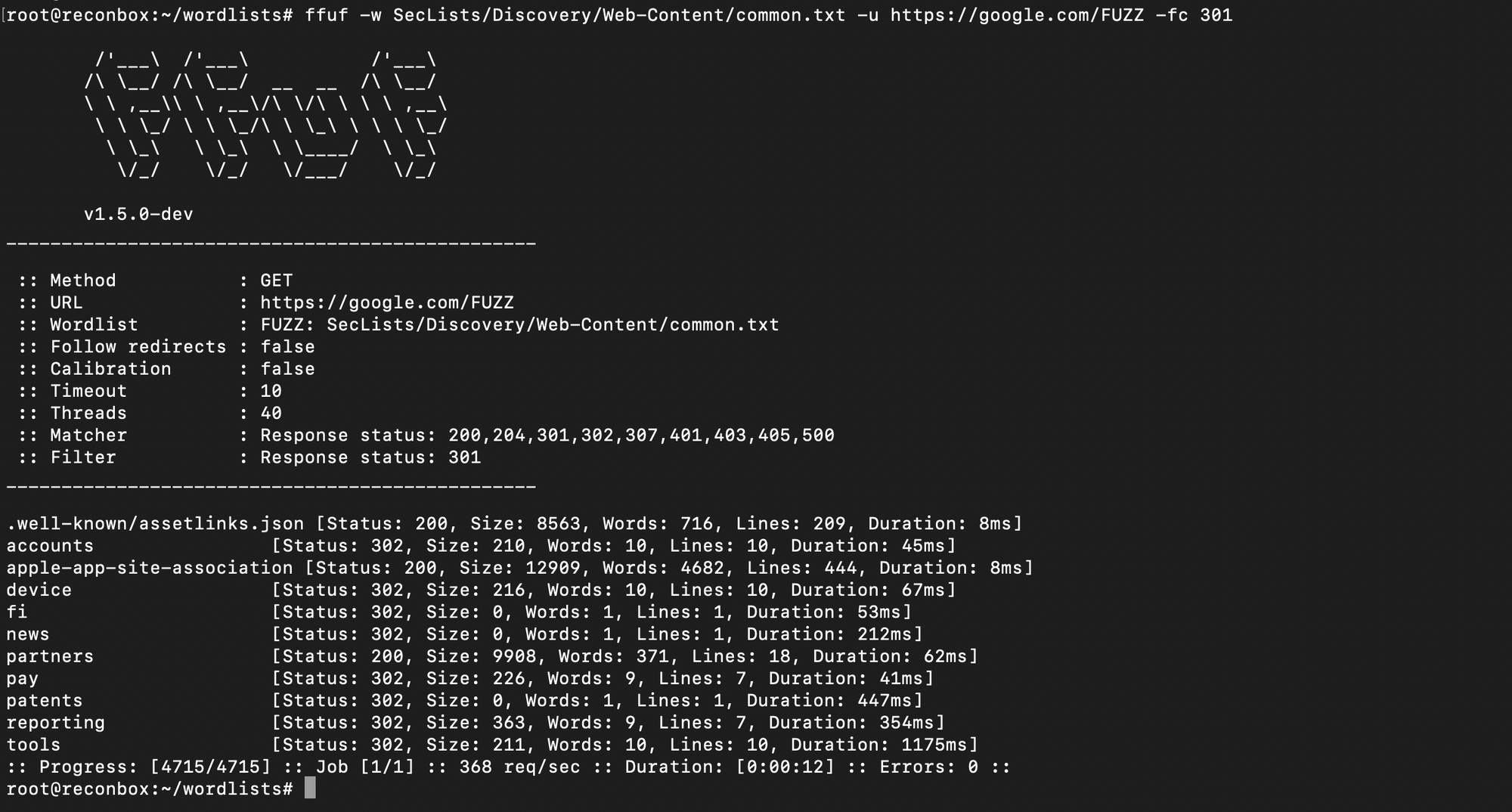
- To only match results with 200 status code, use -mc option (match code)
$ ffuf -w <wordlist.txt> -u https://<target.com>/FUZZ -mc 200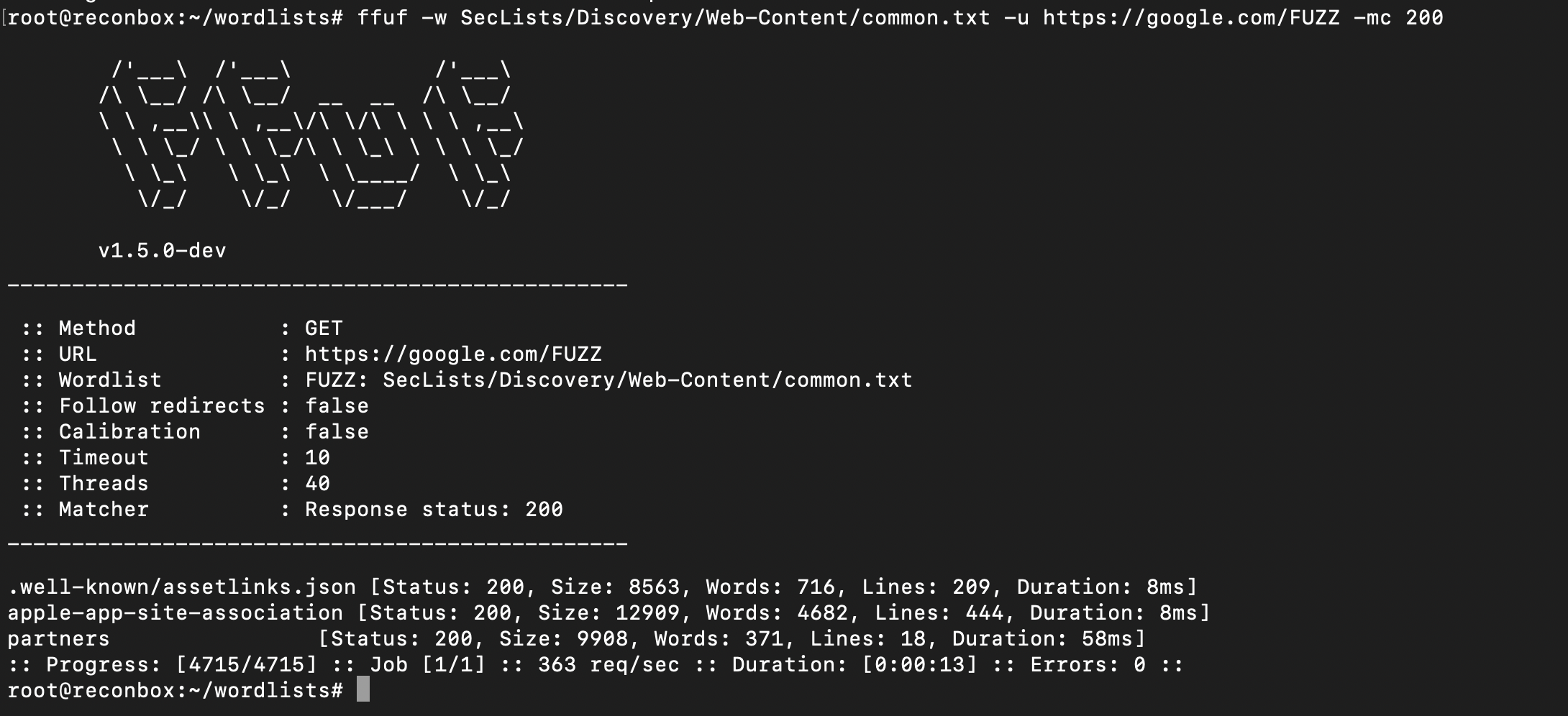
- Well, ffuf has lot of options. Lottttt!! I will cover most of them here.
Redirection and Control
Use -r for follow redirects (301, 302 redirection), -t for threads and -rate for requests/second control.
$ ffuf -r -t 100 -rate 1000 -w <wordlist.txt> -u https://<target.com>/FUZZ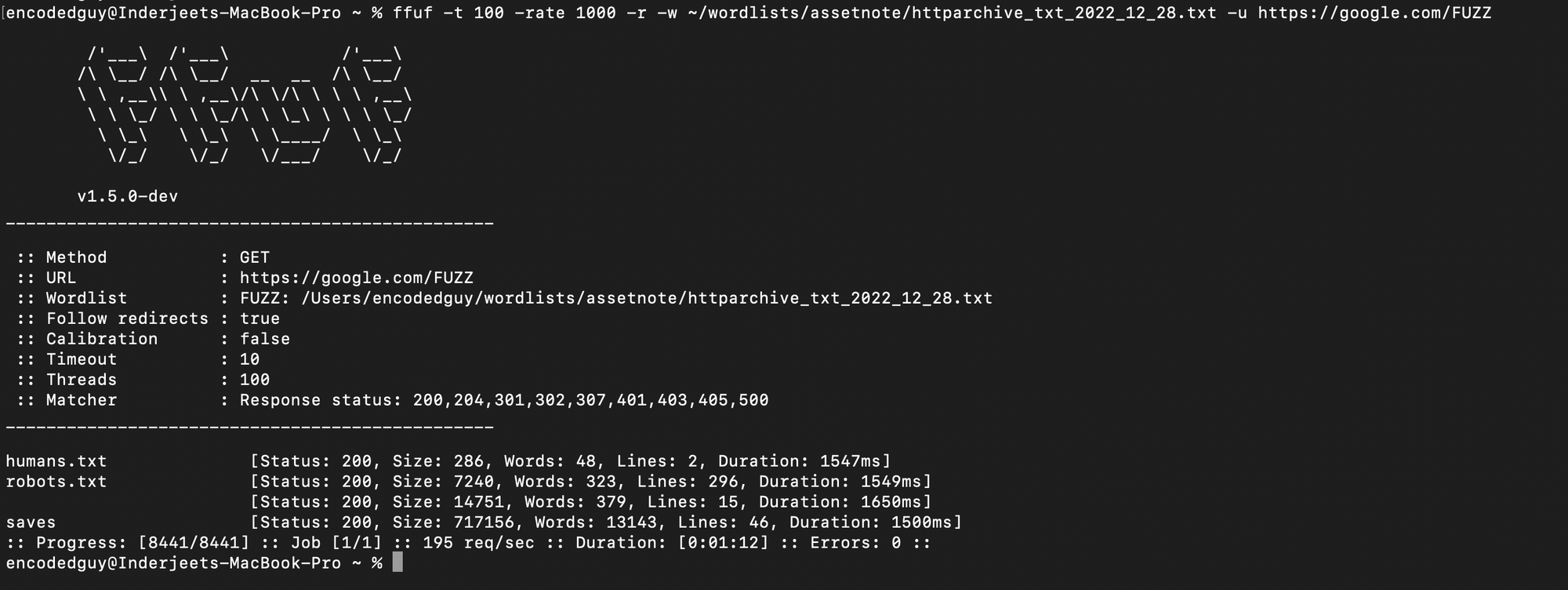
Proxying ffuf traffic
- Use -c to colorize the output, -x to proxy the traffix, -fs for filtering out results by there response size. -fs 0 will not match any results that have zero length.
$ ffuf -c -x http://<IP>:<PORT> -r -fs 0 -w <wordlist.txt> -u https://<target.com>/FUZZ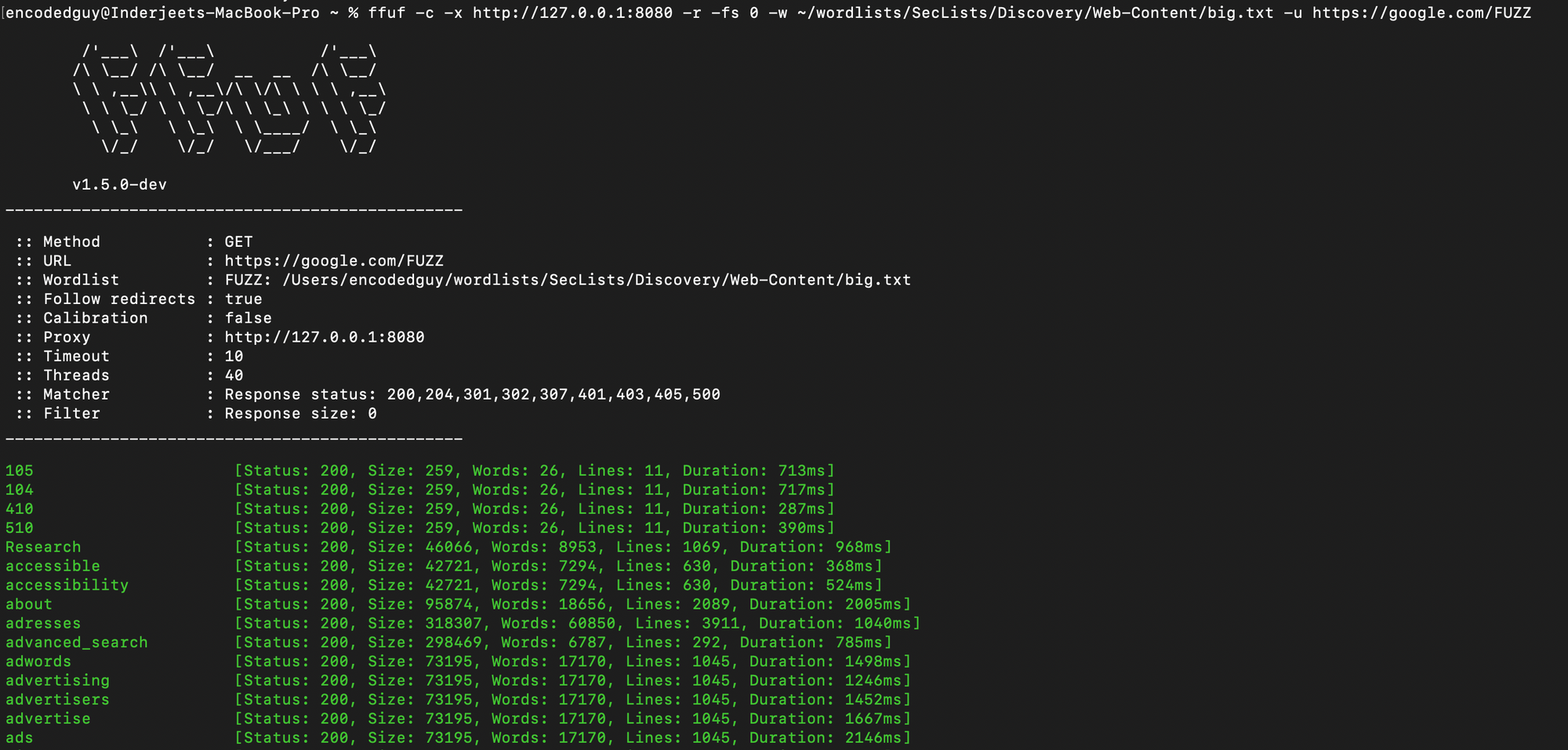
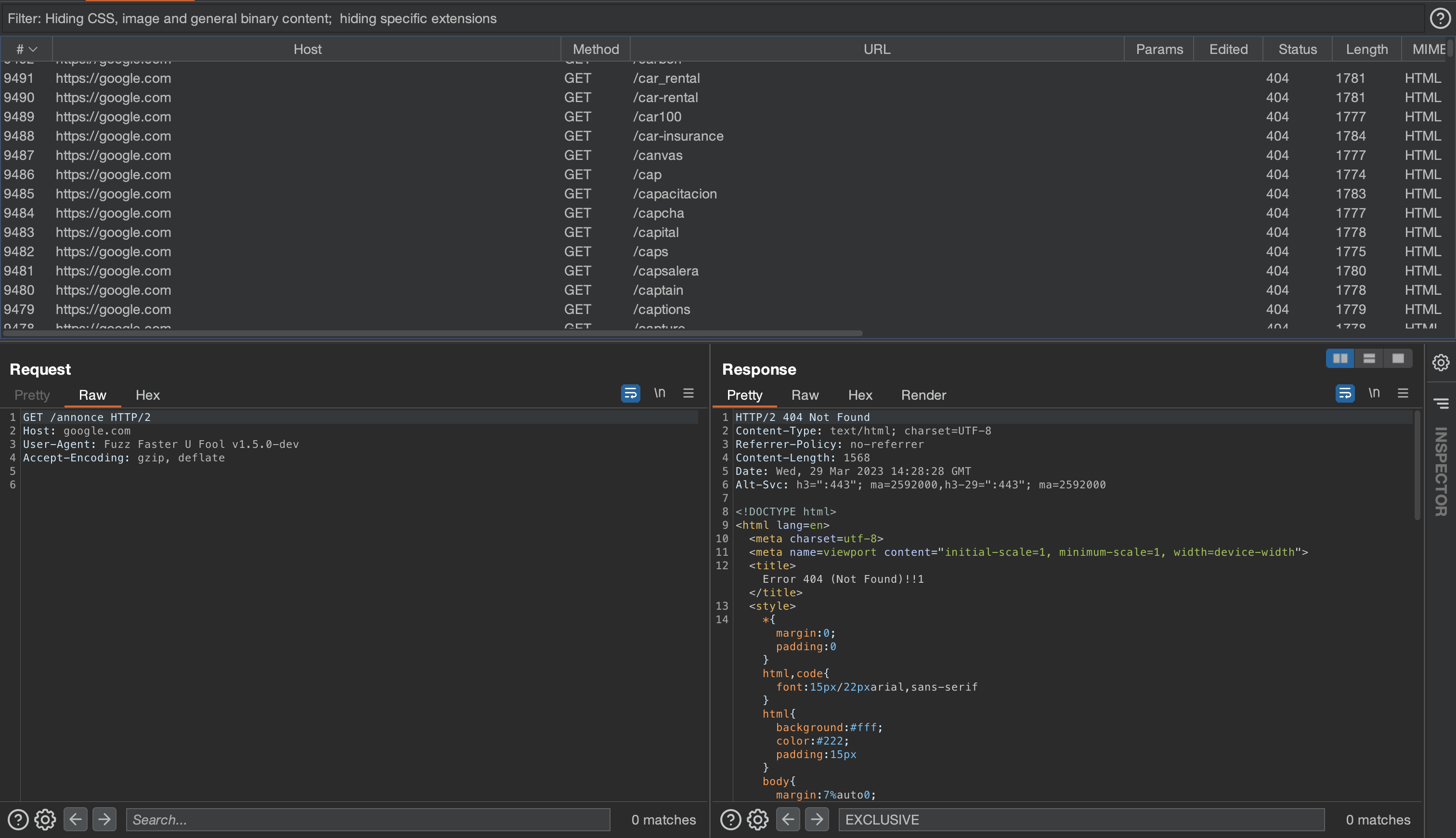
- Proxying traffic is very helpful when we are fuzzing more critical locations inside a request. It helps to debug each request and response properly.
Fuzzing for Subdomains
- You can also fuzz to find subdomains. Just use the FUZZ keyword before the domain part, FUZZ.target.com.
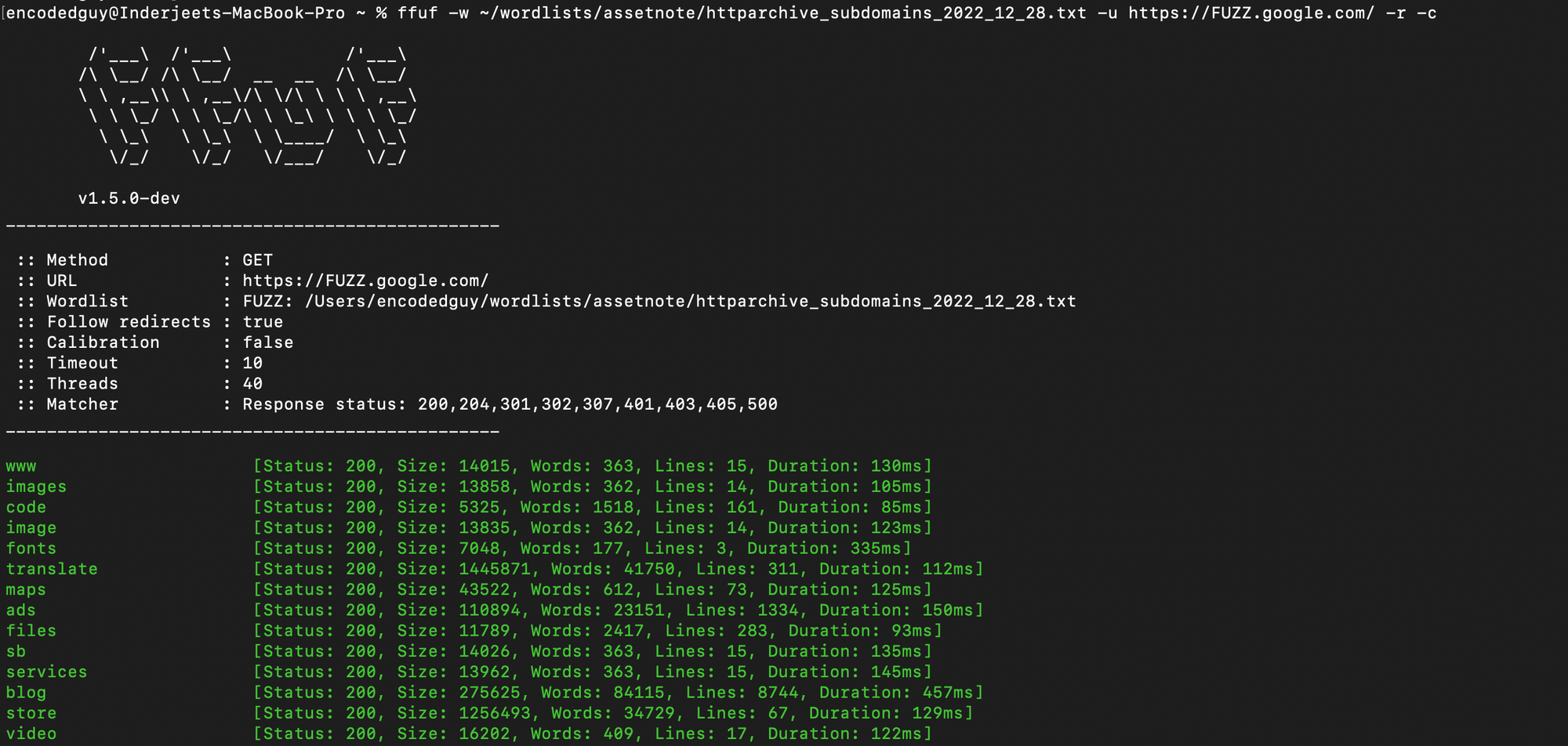
Fuzzing User-Agents
- What about fuzzing a request's User-Agent? Yess, you can FUZZ user agents as well. You can fuzz any place where you will specify this keyword FUZZ.
- Use -H option to specify HTTP headers. User-Agent is also a HTTP header.
$ ffuf -w <user-agents-wordlist.txt> -u https://google.com/robots.txt -H 'User-Agent: FUZZ'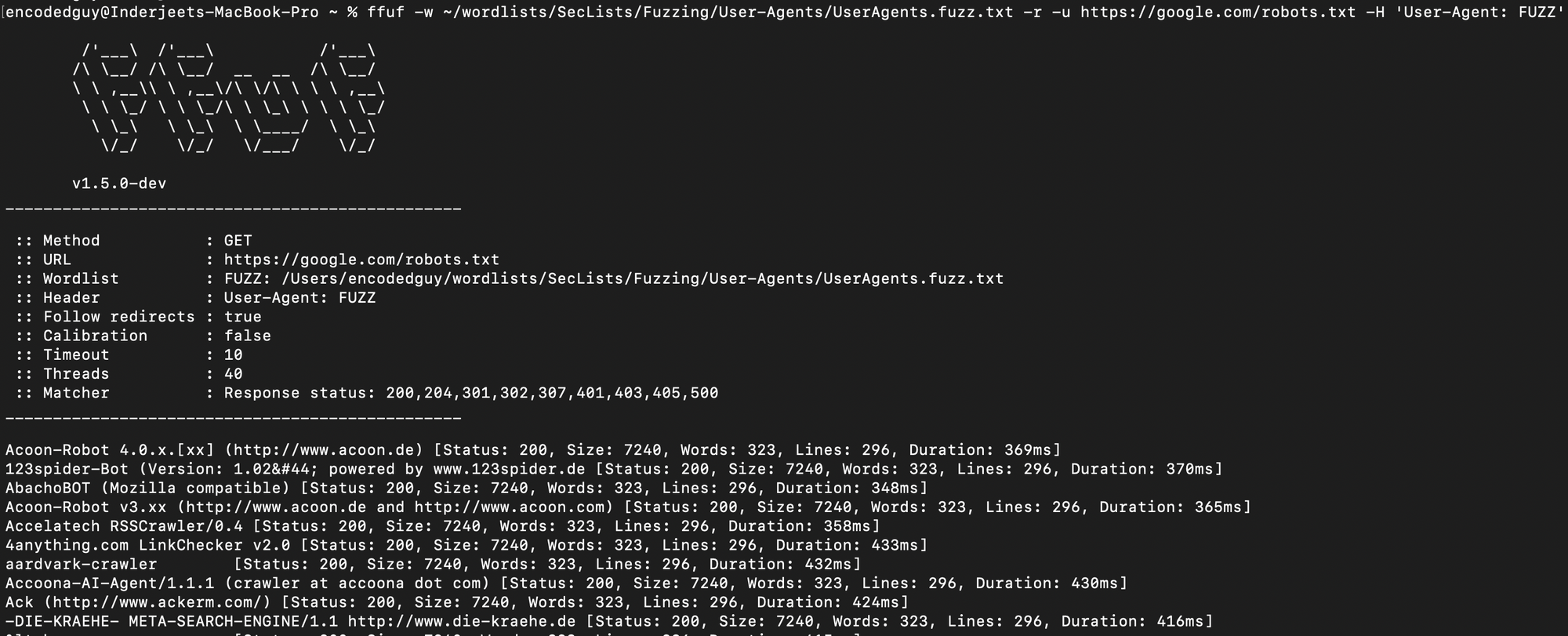
- Sometimes, servers are configured in such a way that response will only be given when particular User-Agent is present in the request. This trick helps to bypass 403/404 errors in some cases. The above one with google.com is just an example, robots.txt is already globally accessible.
Filters
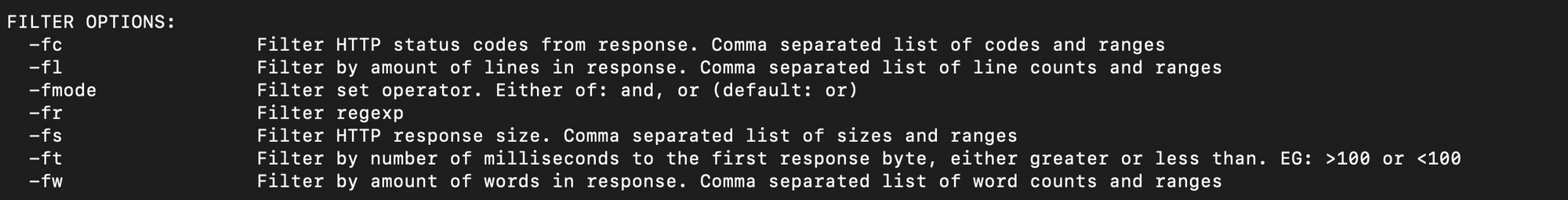
- We have seen -fs option to filter out responses on the basis of response size. ffuf also helps to filter out responses on the basis of lines (-fl), response time (-ft), words (-fw), status codes (-fc), and regex patterns (-fr).
Matchers
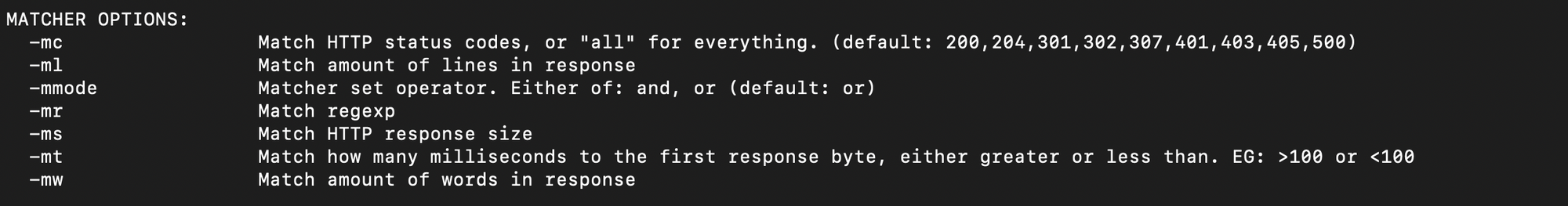
- There are matchers to match particular response codes (-mc), response size (-ms), lines (-ml), words (-mw), etc.
Methods and POST data
- To use POST, PUT, DELETE as method. Use -X option and -d to provide body and here I have used -H to provide Content-Type HTTP header with application/json as value.
$ ffuf -X POST -H 'Content-Type: application/json' -d '{"username":"FUZZ"} -u https://<target.com>/api/username/exists -w <usernames-wordlist.txt>Inputs inside Request
Cookies, HTTP headers, methods, request body, parameters everything can be provided with the options provided in ffuf.
$ ffuf -H <HTTP-headers> -b <Cookies> -X <method> -d <POST-body> -w <wordlist.txt> -u http(s)://<target.com>/- Attacker can use FUZZ keyword anywhere inside cookies, body, headers, URL, etc.
Intruder Attacks
- How to do a sniper attack or clusterbomb attack like we do in Burpsuite Intruder with ffuf? Let me explain how.
$ ffuf -w <usernames.txt>:USER -w <passwords.txt>:PASS -X GET -u https://target.com/login?username=USER&password=PASS -mode <sniper/clusterbomb/pitchfork>Raw HTTP Request
- What about using a raw HTTP request as input? Use -request option. Inside the request write "FUZZ" wherever you would like to fuzz with the wordlist.
- Suppose you have list of user-ids and particular request is vulnerable to IDOR. If the POST data body is too big. Just save the request in a text file. Write FUZZ at the location where you want to fuzz and a wordlist of userids and b00m!!
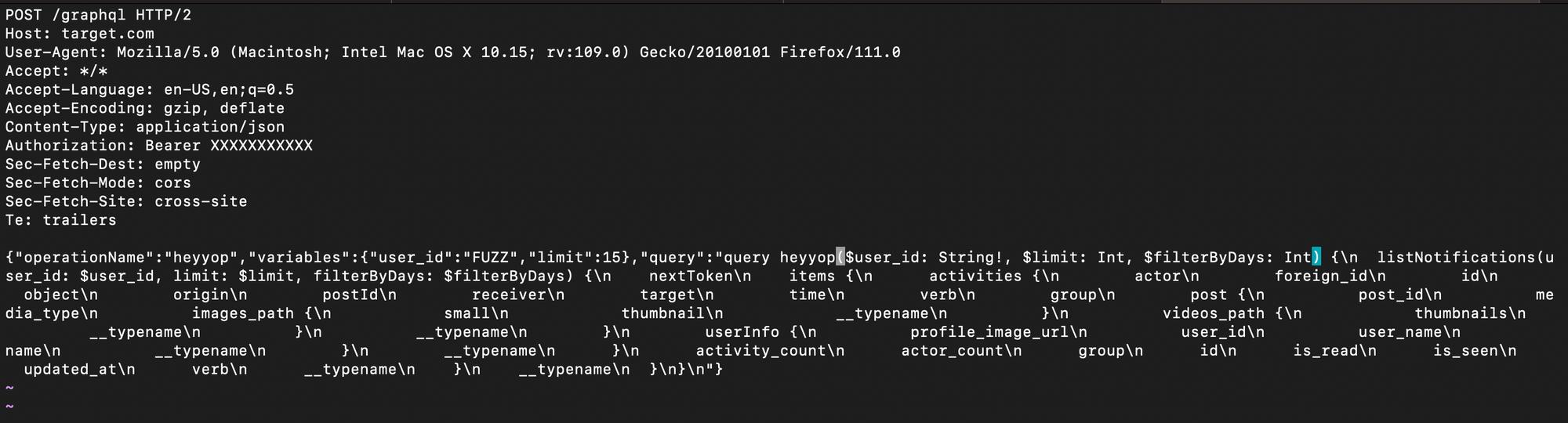
$ ffuf -request http-req.txt -w <wordlist.txt> -c Tips for beginners:
- Use options like -mr to match regex patterns to match strings and regex patterns for sensitive leaks inside responses.
- Filter the responses as much as you can by using options like -fw, -fs and -fl so that you are left with good results only.
- Proxy the traffic using a proxy software like Zap or Burpsuite to visualize what's going on when it is running? How much traffic is flowing and at what rate?
- Control the rate and threads as per the program policies to avoid getting banned from the program.
Inderjeet Singh
Want some help, message me on Twitter @3nc0d3dGuY
Happy Hacking!!