How do I approach exploiting access control bugs?
Hi,
I am Inderjeet Singh, a student in the morning and a bug bounty hunter in night. Today I will write about access control issues and why or why shouldn't you use Autorize or some automated extension to hunt for this bug.
Access Control Vulnerabilities
Let's talk about access control first. When you open an application there are multiple functionalities present there ranging from uploading a profile photo, editing your name, reading your transactions, deleting a comment, etc.
Developers, when they write code they enforce some access control on these functionalities so that another user cannot execute these functionalities on your behalf. Basically, if you are opening your bank account only you are authorized to access or change anything in your account. If someone else (a hacker) can access, edit or delete any data in your account, it is known as an access control vulnerability.
How I Approach Access Control Vulnerabilities?
I will start by browsing the application and I will check all the possible features like edit result, read invoices, delete history, create comment, etc. After this, I will see if I can create multiple user roles in the app or not, if yes, then it's a multi-tenant application that is more fun to hack with access control bugs.
Now, I will define some testing scenarios for testing my application:
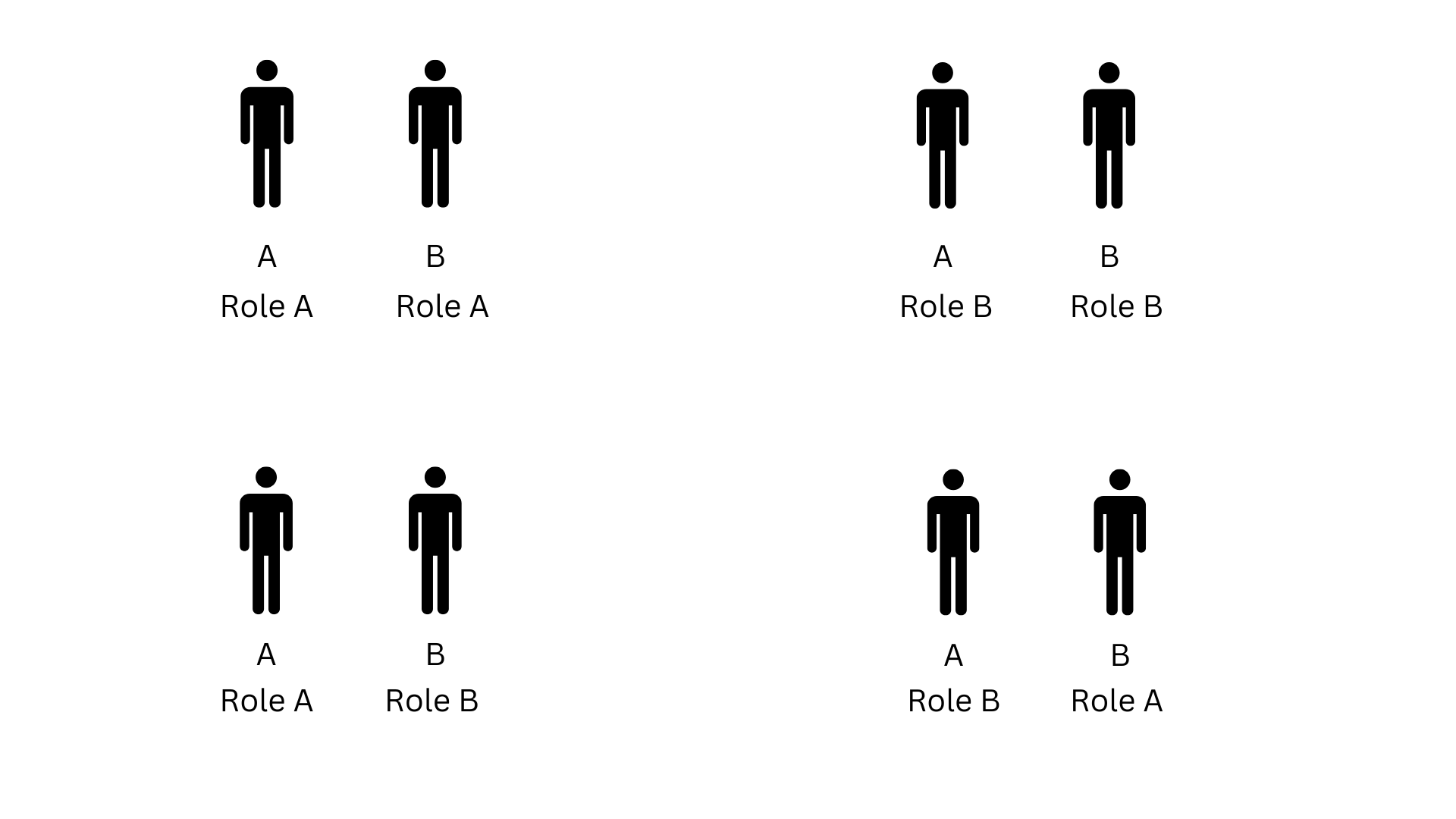
- If there is only single user role in the application. Create two users A and B. I will use the whole application with cookies or access token of User A. With the same cookies or access token, I will try to read or modify User B's resources.
- If there are multiple user roles, suppose there are two roles present in the application: Admin and User. In this case, testing scenarios are even wider.
- Horizontal Access: Create two accounts of same roles: A and B. I will test in the same way as in Step 1. If some unauthorized access is found, then this is Horizontal Unauthorized Access.
- Vertical Access: Create two accounts of different roles: User A and Admin B. I will use the application with User A and with the same cookies/token, if I can read or modify the resources of Admin B, this is Vertical Unauthorized Access.
- Summary of Testing Scenarios: Role A - Role A, Role B - Role B, Role A - Role B, and Role B - Role A.
Why There are always Access Control Bugs?
Well, I want to answer this question the way "InsiderPhd" said in her videos on Youtube.
Suppose the application has 50 features and 2 user roles. This means I will have to test 100 possibilities first for Role A - Role A, then 100 again for Role B - Role B, then 100 more for Role A - Role B, and 100 more for Role B - Role A. This is testing 400 possibilities. And, there comes CRUD. CRUD stands for Create, Read, Update and Delete. So, if an application has 1 feature, that feature in general will have 4 endpoints (C-R-U-D). So, now we have more than 1600 possibilites (400 x 4).
If testing 1 scenario takes approximately 1 minute, then 1600 will take 1600 mins that is appoximately 27 hours (20 mins for Redbull!). Here, you will not only test for access control bugs, you will also do Recon, find XSS, SSRF, CSRF, Authentication flaws, File Upload bugs, business logic errors, and other flaws. Right? This means just to test for this one OWASP Category Broken Access Control, you will need to devote 27 hours in this case. This number will vary up and down depending on the number of features, and number of roles in the application. Let's talk about automating this now.
Autorize: Automated Testing
Well, here comes Autorize to save your time. Believe me when I say, "Autorize is the best thing an attacker can use", it is.
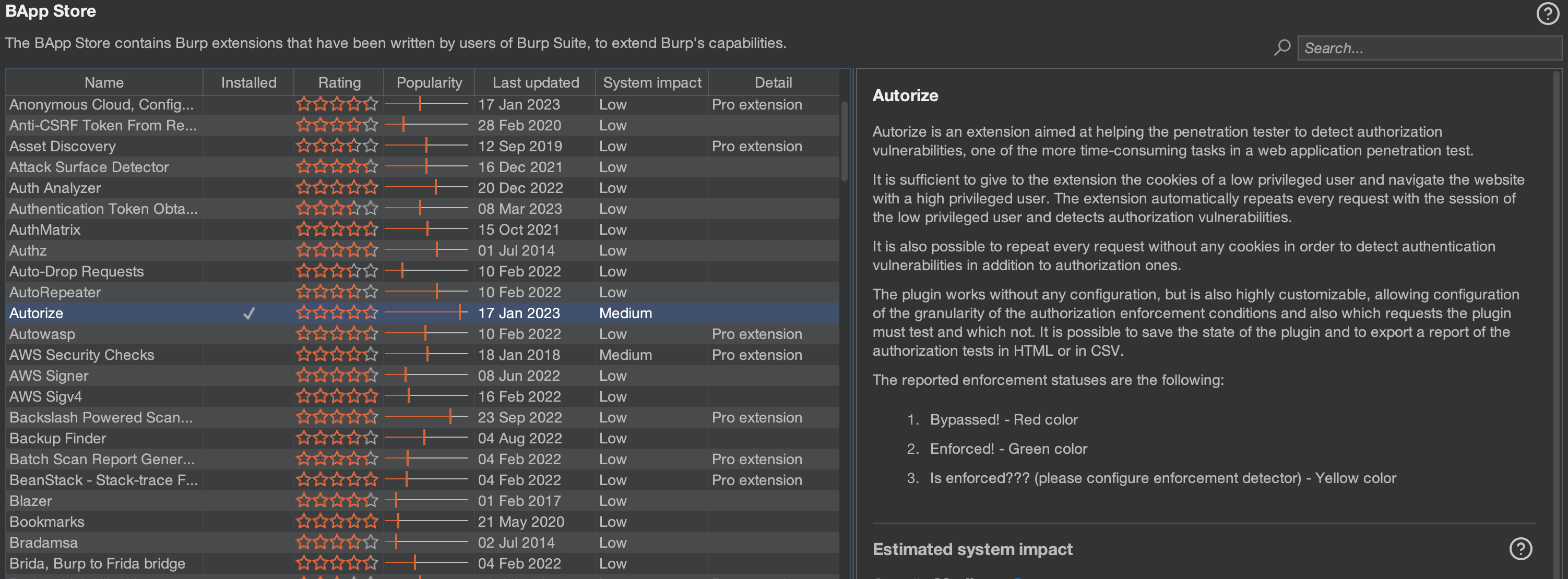
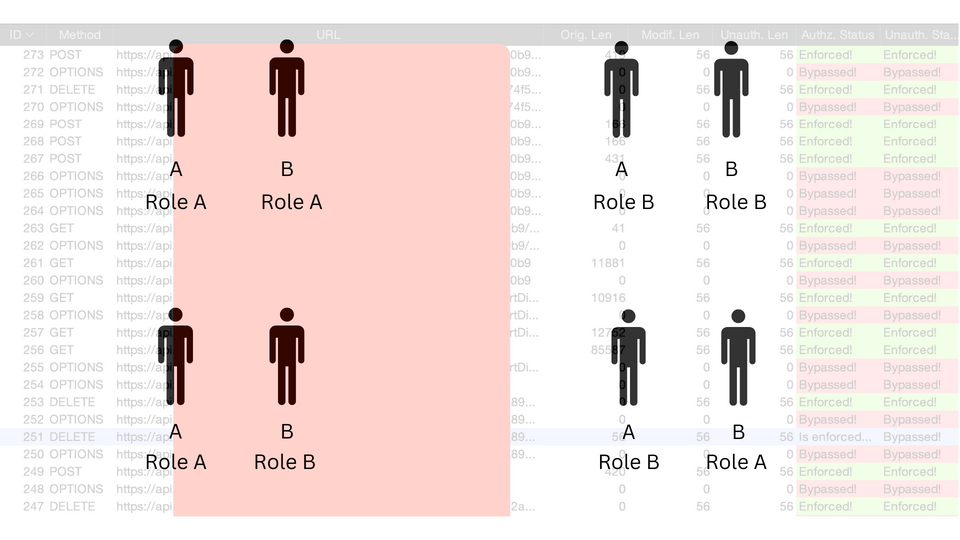
Autorize is a Burpsuite extension, that you can Install from BApp Store and it is also available for Burpsuite Community Edition. In the Configuration part of Autorize, tester can put the cookies of User B and browse the whole application with User A.
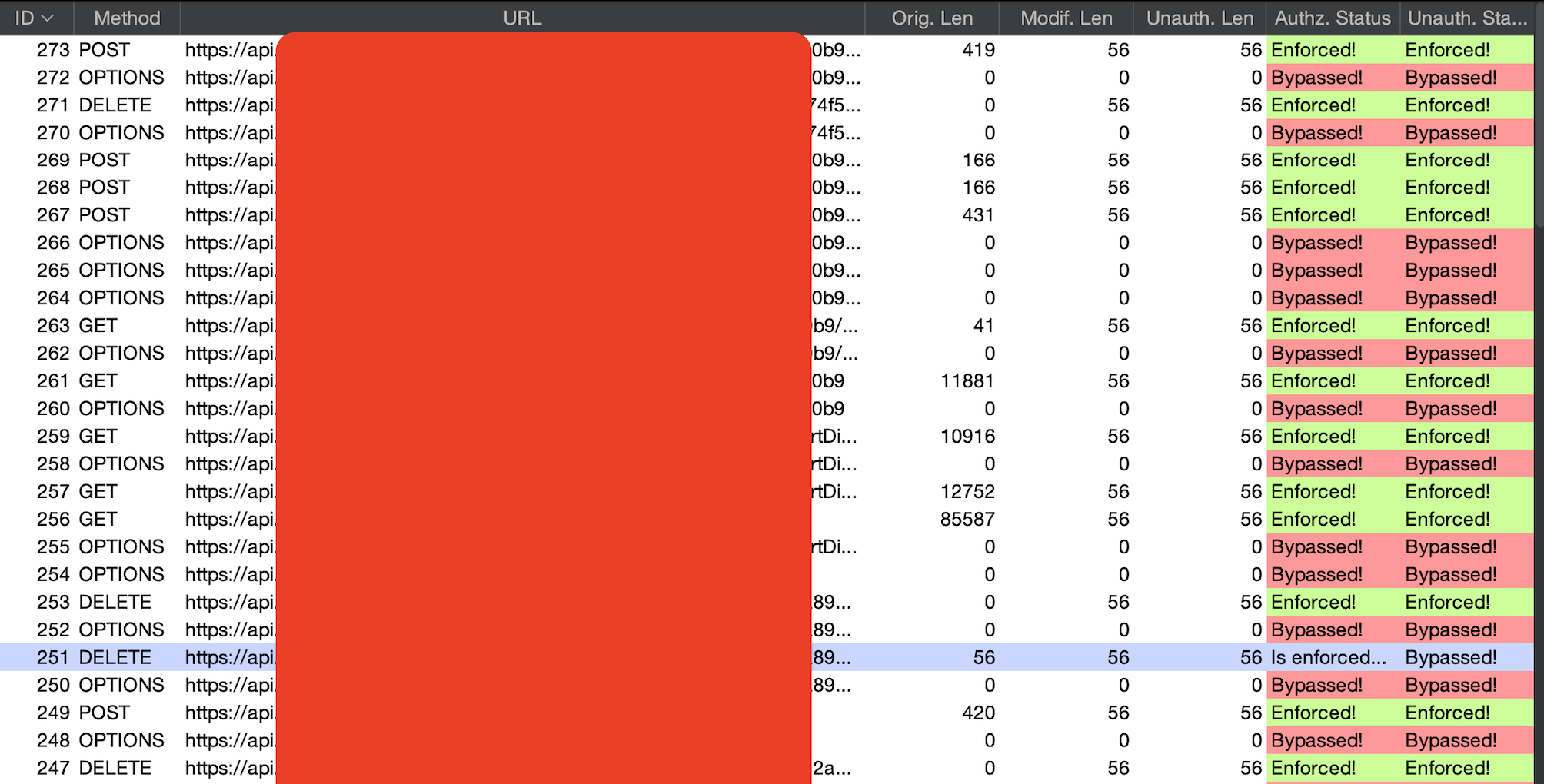
Autorize will automatically make three requests one with User A's cookies/tokens, second with User B's cookies/tokens and third request is unauthenticated by removing the cookies/tokens. So, if any endpoint or resource that you are using from User A's perspective, the same endpoint or resource is also requested by User B. If any unauthorized access is present, Autorize shows "Bypassed". In case of proper access controls, it shows "Enforced", and if it's unsure then it says "Is enforced?".
Autorize can't test everything
Don't rely on automated testing tools like Autorize, Autorepeater, etc. for everything. I have found so many cases when Autorize didn't detected that case but I found the improper authorization manually in Repeater. Always verify your "Bypassed" cases found in Autorize manually in Repeater and test the "Is Enforced?" cases as well in Repeater.
Autorize can't test:
Some vulnerabilities that also fall in access control vulnerabilities:
- Mass Assignment attack
- Parameter pollution
- 403 Forbidden Endpoint Bypasses
- Null byte injections
- Testing negative values, long values, etc. for exposures.
- Appending .json at the end of endpoint
- This is not the end, there are many ways to achieve unauthorized access
Conclusion: East and West, Manual is best!!
My Handles: Twitter Hackerone Github
Thank you for reading!!
Happy Hacking!!