Hacker's Guide to Directory/Endpoint Enumeration

What is Directory Enumeration?
Directory enumeration is when the hacker tries to find more public or hidden/private directories. The root directory of a web server starts from /var/www/<site>. https://rashahacks.com is hosted at /var/www/rashahacks.com
Directories
If you will go to the source code of any site, you will see many other directories like /static, /content, /content/images, /static/js, etc. These directories contain more files and sub-directories.
Today developers define an endpoint that serves a particular file or directory. Like, /login endpoint will serve the /static/html/login.html file.
How to do Enumeration?
- Target URL
- Wordlist
- Directory Fuzzer
- Rate Limitation Policy
Target URL is the most important factor during fuzzing.
Enumerate this: https://example.com/FUZZ
Enumerate this also: https://example.com/admin/FUZZ
Many hackers do directory enumeration at https://example.com/<FUZZ>. Imagine a scenario where you found /user/tickets/ endpoint in a Javascript file but it is 403 Forbidden. Try to enumerate endpoints here, maybe /user/tickets/4623 is a valid ticket number responding with the details of the ticket.
Try all the HTTP methods, GET, POST, DELETE, PUT, etc.
Wordlist
A wordlist is the second most important factor in directory enumeration. Let me give you a very straightforward example to understand why I am saying so.
If you are targeting a PHP server, then it's obvious that you won't find anything by using a word list of .asp, and .aspx extension files. You need a wordlist containing files like admin.php, config.php, etc.
Choose a Fast Fuzzer
When thousands of other hackers are also hacking with you on the same endpoint, you definitely won't follow the tortoise-rabbit strategy, you have to be the shark of the ocean.
My personal choice is ffuf: https://github.com/ffuf/ffuf

With ffuf, you can fuzz directories, subdomains, HTTP methods, headers, and anything that you want. Other than this, at one target URL, you can fuzz two places at the same time.
https://example.com/<FUZZ1>/<FUZZ2>
I have this write-up in the draft on "How I use ffuf to enumerate everything?". Subscribe to the blog newsletter to get updates.
Rate Limitation Policy
Read the policy of the program, if it says 20 requests per second. Enumerate endpoints at the rate of 20 req/sec.
ffuf -u https://example.com/api/users/<FUZZ> -w endpoints.txt -rate 20 -t 1
Change the -rate flag to change the req/second rate.
Directory enumeration
- Target URL with -u flag
- Wordlist (Useful one) -w flag
Very Simple Fuzzing
ffuf -w php-wordlist.txt -u https://example.com/admin/FUZZ
FUZZ keyword is required to tell ffuf were to enumerate.
Little Advance Fuzzing
ffuf -w users.txt:USER -w passwords.txt:PASS -u https://example.com/login -X POST -d "username=USER&password=PASS" -rate 10 -t 1 -fc 403,401 -r -mr "Login Success"
- Defining two wordlists: USER for users.txt and PASS for pass.txt
- -X for HTTP method (POST here)
- -d for POST data (username=USER&password=PASS)
- -rate to not exceed 10 requests per second
- -t 1 for single thread, -t 2 means two concurrent threads
- -fc 403,401 for not getting Forbidden and Unauthorized responses in output
- -mr for matching the response containing a string "Login Success"
- -r for following redirects like 302 and 301.
Read the readme file from ffuf for more options: https://github.com/ffuf/ffuf#readme
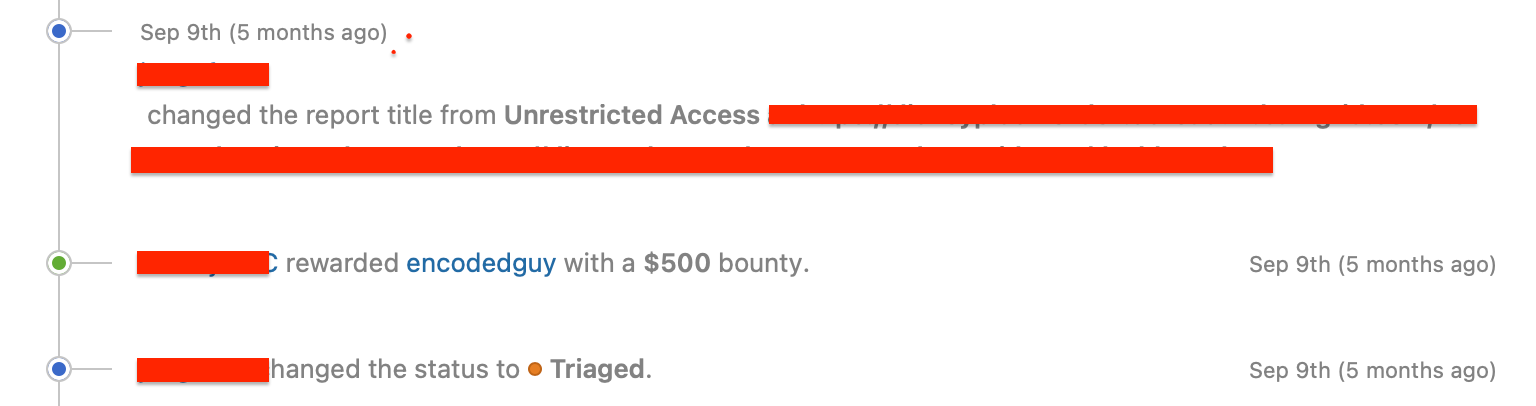
Example: Simple 500$ Finding from directory enumeration
In September 2022, I was invited to a private one-month challenge on Hackerone. The target was very wide.
Steps
- Got a host which was giving 403 Forbidden but it was a little suspicious looking at it.
- I did directory enumeration and /dashboard endpoint was accessible giving access to the admin panel.
- As that panel was not very sensitive, the triager triaged it with medium severity and rewarded 500$.
Subscribe to the newsletter to keep receiving updates for new posts.
The perfect mixture of spices and vegetables equals delicious food. The perfect combination of wordlist and target URL leads to delicious bugs.