How I Earned $150 for Reporting a Security Flaw

Hey everyone!
root@icyberjutsu:- # whoami

My name is Aman Kumar(icyberjutsu), and I am a cybersecurity researcher based in India. Hope you all are doing great.
This is the story of my first bounty; I was evaluating a program and discovered a vulnerability that could lead to a security breach. In this write-up, I will be detailing the steps I took to discover the vulnerability and the impact it could have had if left unchecked.
Subdomain Enumeration:

My first step in evaluating the program was to perform subdomain enumeration on the target website. This involves searching for subdomains associated with the target website that may have vulnerabilities or misconfigurations. After completing subdomain enumeration, I came across an endpoint on a subdomain that allowed users to change their account email.
Discovery of Vulnerability:
As I was testing the endpoint, I realized there was no rate limit on how many times a user could change their email address. This led me to consider changing the email address to a victim's email. My curiosity led me to turn on "hacker mode," and I began exploring this vulnerability's potential impact.
Severity and Tool Used:

After analyzing the vulnerability, I determined it was low severity, with a severity score of 3.0-4.0. The tool I used to analyze the vulnerability was Burp Suite, commonly used by cybersecurity professionals for web application testing and analysis.
Vulnerability Description:
The vulnerability I discovered was related to the lack of a rate-limiting algorithm for changing account email addresses. Rate limiting is a strategy for limiting network traffic. It determines how often someone can repeat an action within a specific timeframe — for instance, trying to log in to an account.
Impact of Vulnerability:
If the company is using any email service software API or some tool that has been bought for the emails being sent on the support domain, the rate limit can result in financial loss, and it can also slow down your services as huge/mass emails will lead to disruption of data that original user might send or the quota that has been bought might be exhausted.
Steps to Reproduce:
- Open this link: https://subdmoain.target.com/edit-profile/
- Intercept the request in Burp Suite.
- Send the request to the intruder.
- In the position tab first clear everything.
- Add any position. (For E.g. - I select “0.5”)
- Use null payloads and set the payload count.
- Click on "Start Attack".
- The victim will receive the emails in their inbox.
How I Discovered the Vulnerability:
- I created an account on the example.com web application.
- I discovered that I could change my account email.
- I changed the registered email to a new email.
- Before clicking on save change, I turned on Intercept and captured the request.
Report Timeline:
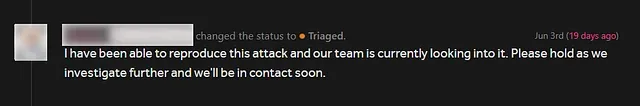
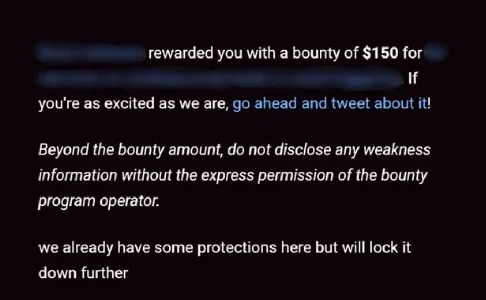
I reported the vulnerability on June 3, 2022, and it was reviewed and triaged on the same day. The vulnerability was assigned a severity score and a bounty amount of $150 was offered. The vulnerability was resolved, and the report was closed on June 8, 2022.
Thank you for taking the time to read my write-up! If you found it interesting and informative, please give it a round of applause and follow me for future updates. I would love to hear your thoughts on this piece, so don't be shy and leave a comment down below!
So, let's connect and continue exploring the exciting world of cybersecurity together!
Connect with me:
Happy Hacking :)